I have done several testbed to looks details on the De-Auth frames.
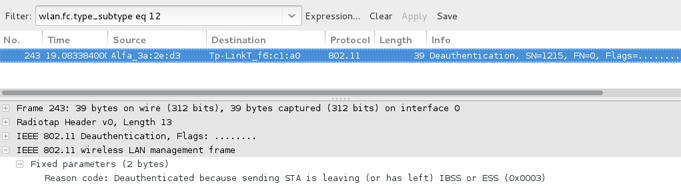
This is the legit de-auth packet sent from client to AP.
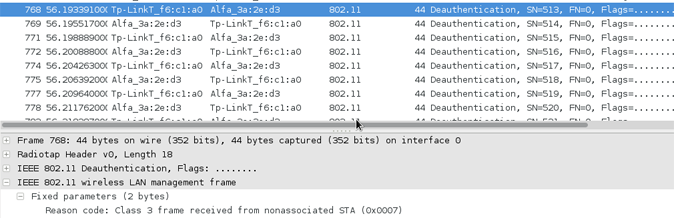
Here is De-Auth packet sending by aireplay-ng with command :
aireplay-ng -0 1 -a 10:FE:ED:F6:C1:A0 -c 00:1F:3C:E4:AF:7F mon0
Where :
-0 - Means deauthentication
1 - Number of deauth
-a 00:14:6C:7E:40:80 - MAC address of deauth packet
-c 00:0F:B5:34:30:30 - MAC address of station mon0 - the interface name
So what we have here ?
1. The legitimate de-auth packet just send only 1 packet to de-auth
2. The legitimate de-auth packet length is 39 bit where malicious de-auth sending 44 bit length
3. De-auth attacks using aireplay-ng with 1 deauth will send 128 packet which is 64 packet to the AP and 64 to the Client as depicted above.
4. On the reason code for the legit deauth is Code 3 that is sending STA is leaving, but from the malicious deauth packet send Code 7 – Class 3 received from non associated station.